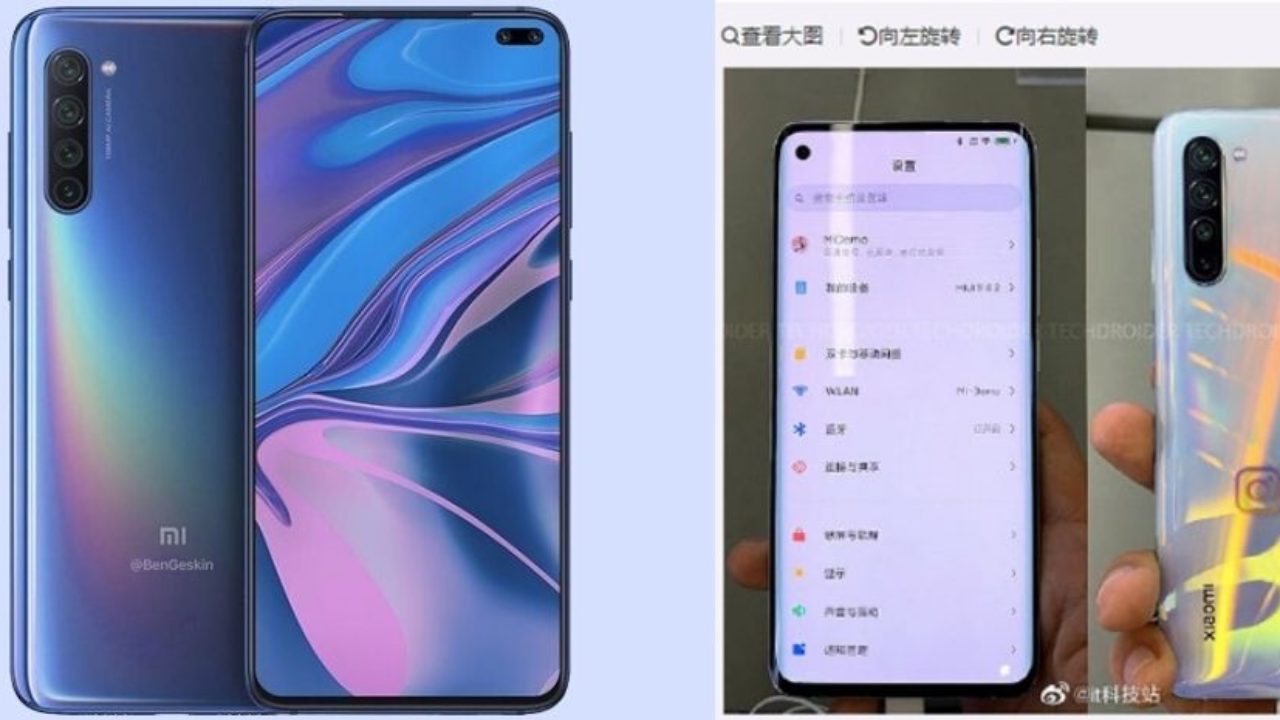
Mi 10 spy
Compatibility To confirm that this part fits your vehicle, please enter your vehicle's details below. Year: Select. This part is compatible with 0 vehicle s. Show all compatible vehicles. This part is compatible with 1 vehicle s matching. Recent searches. Shipping Methods The total estimated time it takes to receive your order is shown below:.
You place your order Processing time We ship your order Shipping time Delivery! Total Estimated Delivery Time. The total delivery time is calculated from the time your order is placed until the time it is delivered to you.
Xiaomi Mi 10 Pro Spy Photos And Rendering Of Transparent Edition
Total delivery time is broken down into processing time and shipping time. Processing time: The time it takes to prepare your item s to ship from our warehouse. This includes preparing your items, performing quality checks, and packing for shipment. Shipping time: The time for your item s to travel from our warehouse to your destination. Ship to: Germany. Ship From CN Warehouse. Payment methods We support the following payment methods. Click for more information if you are confused about how to pay.
We will send a confirmation code to your mobile phone to verify that your contact details are correct. Please ensure you follow all the instructions contained in the message. Bulk Buy Discounts Order 3 or more and enjoy the savings. Bulk prices will be shown in the shopping cart.

Wholesale Inquiry Product Name. Customer Note. Customer Name. Country: United States. Customer Reviews. Searching for relevant results You Viewed. Related Searches:. My Messages. My Coupon.
- Alleged Xiaomi Mi 10 Spotted In Spy Photos.
- Best Restaurants in Spy, Walloon Brabant Province.
- Parc de realite virtuelle Terragamecenter.
- THE 10 BEST Restaurants in Spy - Updated March - Tripadvisor?
- app to locate smartphone Oppo RX17;
- software to location phone Nokia.
- "They didn't succeed.".
Help Center. Expect to see Xiaomi and Google abandon the Mi A1 altogether by the end of the year. Source s. Related Articles.
The Xiaomi Mi A3 receives a new und The core iKF matches the This was reported in for XP and Vista, and it seems that Microsoft used the same method to push the Windows 10 downgrade to computers running Windows 7 and 8. Microsoft has backdoored its disk encryption. Here is a suspicion that we can't prove, but is worth thinking about: Writable microcode for Intel and AMD microprocessors may be a vehicle for the NSA to invade computers, with the help of Microsoft, say respected security experts.
Windows 8 also has a back door for remotely deleting apps. You might well decide to let a security service that you trust remotely deactivate programs that it considers malicious.
Chateau d'Ice Spy
But there is no excuse for deleting the programs, and you should have the right to decide whom if anyone to trust in this way. The article additionally highlights the pitfalls of DRM. This is another proof that a DRM-encumbered product doesn't belong to the person who bought it. Microsoft said it will refund customers, but this is no excuse for selling them restricted books. DRM in Windows , introduced to cater to Bluray disks. The article talks about how the same malware would later be introduced in MacOS. That had not been done at the time, but it was done subsequently.
We mention them to refute the supposition that prestigious proprietary software doesn't have grave bugs.
Account Options
Exploits of bugs in Windows, which were developed by the NSA and then leaked by the Shadowbrokers group, are now being used to attack a great number of Windows computers with ransomware. A flaw in Internet Explorer and Edge allows an attacker to retrieve Microsoft account credentials, if the user is tricked into visiting a malicious link.
Point-of-sale terminals running Windows were taken over and turned into a botnet for the purpose of collecting customers' credit card numbers.
This section gives examples of Microsoft software harassing or annoying the user, or causing trouble for the user. One version of Windows 10 harangues users if they try to install Firefox or Chrome. Microsoft is planning to make Windows impose use of its browser, Edge, in certain circumstances. Windows displays intrusive ads for Microsoft products and its partners' products.
Xiaomi Mi 10 Pro Spy Photos and Rendering of Transparent Edition
We disagree. To do this, Microsoft used malware techniques. A detailed analysis of Microsoft's scheme is available on the Electronic Frontier Foundation's website. Those machines will be stuck with the nastier Windows Of course, Windows 7 and 8 are unethical too, because they are proprietary software.
But this example of Microsoft's wielding its power demonstrates the power it holds. Free software developers also stop maintaining old versions of their programs, but this is not unfair to users because the users of free software have control over it. If it is important enough to you, you and other users can hire someone to support the old version on your future platforms. The wrongs in this section are not precisely malware, since they do not involve making the program that runs in a way that hurts the user.
But they are a lot like malware, since they are technical Microsoft actions that harm the users of specific Microsoft software. Microsoft repeatedly pushed faulty versions of this program to users' machines, causing numerous problems, some of which critical.